Why?
kube-prometheus is an open-source project created by the maintainers of Prometheus Operator. It provides a set of configuration files and resource definitions for deploying a complete Prometheus monitoring stack on Kubernetes.
kube-prometheus utilizes Prometheus Operator to set up and manage the following components:
- Prometheus: Used for collecting and storing metric data.
- Alertmanager: Used for handling alerts.
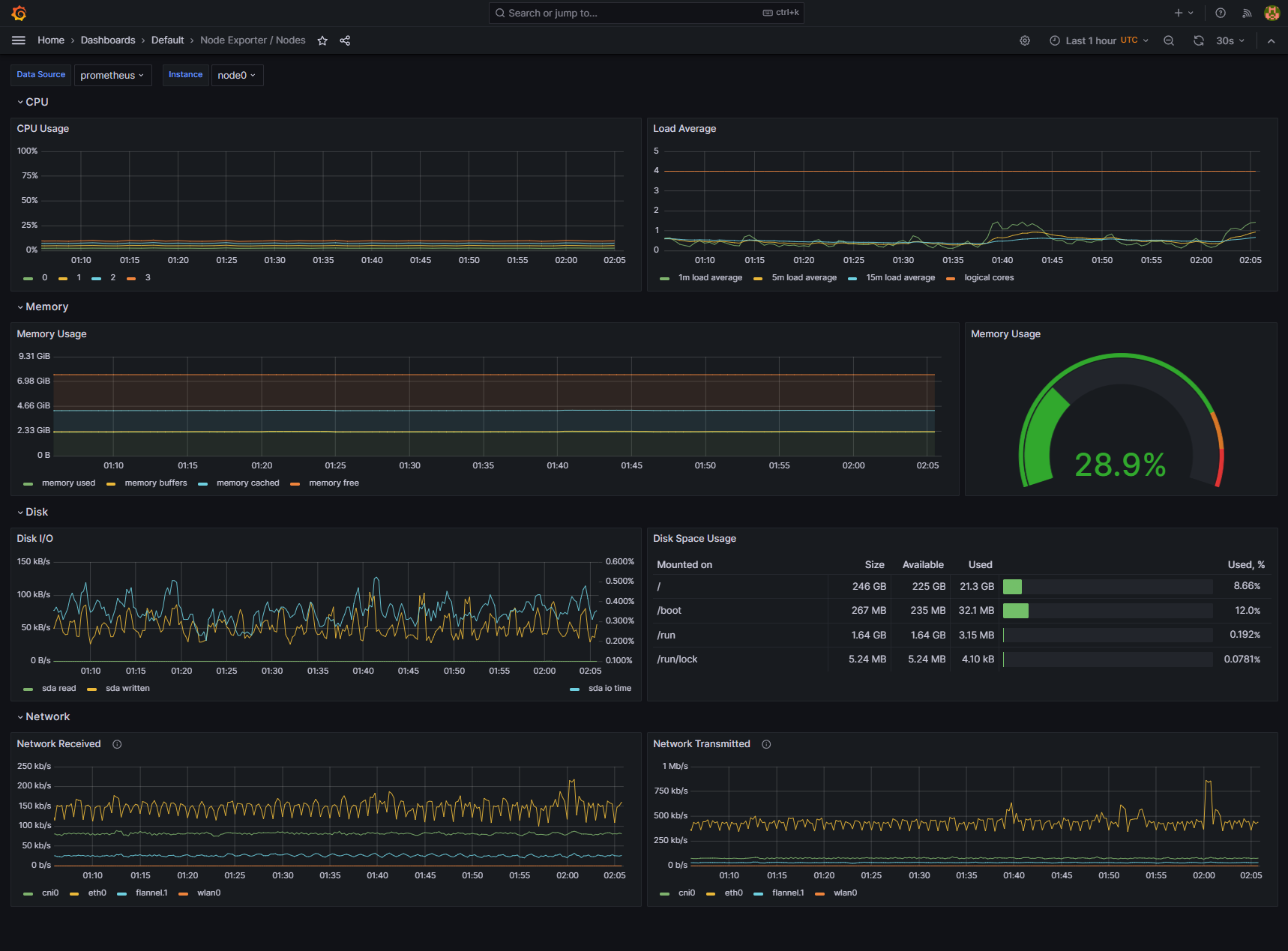
- Grafana: Used for visualizing metric data.
- Prometheus node-exporter: Used for collecting metrics from k8s nodes.
- kube-state-metrics: Used for collecting metrics from the k8s API server.
- Prometheus Adapter: Used for exposing Prometheus metrics to the k8s custom metrics API.
Pros:
- Complete solution: It provides everything needed to establish a comprehensive monitoring infrastructure on Kubernetes.
- Out-of-the-box functionality: Preconfigured alerts and dashboards allow you to quickly start monitoring your cluster and applications without the need to configure everything from scratch.
- Customizable: Although kube-prometheus provides a complete starting point, you can freely adjust and extend it according to your specific requirements.
- Community support: As part of the Prometheus Operator ecosystem, kube-prometheus benefits from an active community that continuously contributes new features, bug fixes, and improvements.
Cons:
- Complexity: kube-prometheus introduces a considerable number of components and configurations. Understanding and managing these require some time and effort.
- Resource overhead: Running a full monitoring stack can consume a significant amount of resources, however does not seem to be the troubling for my little k3s cluster
- Upgrade management: Over time, managing upgrades of the kube-prometheus components can become challenging.
Prepare kube-prometheus Library
The prerequisites specified that kubelet configuration must contains following flags:
--authentication-token-webhook=true--authorization-mode=WebhookFrom what I checked, the k3s agent from the latest version (1.22 and above) already have them included, so we should be good.
kube-prometheus provided the installing guide for anyone who wants to customize the configuration:
| |
Note that when jb install github.com/prometheus-operator/kube-prometheus/jsonnet/kube-prometheus@<release-version> choose the release that’s compatible with the cluster version
Customization for Metallb
I have deployed Metallb for the services on my k3s cluster which works great, and I want to use it to expose Grafana, Prometheus and Alertmanager, so I can access them easily without needing to port-forward lol
With kube-prometheus, it’s pretty simple, just override the service config:
| |
Note that I also override NetworkPolicy for them to allow all ingress traffic, otherwise the default config only allows Prometheus to access them. Technically I should fine grain this config, but since everything runs in my LAN which has no exposure to Internet, I think it should be fine.
Build and Install
Run ./build.sh in the folder (e.g. my-kube-prometheus) will generate all the manifests in manifests folder. Then just install with kubectl
| |
That’s it.